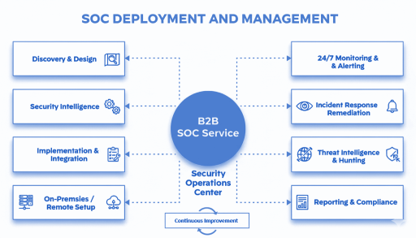
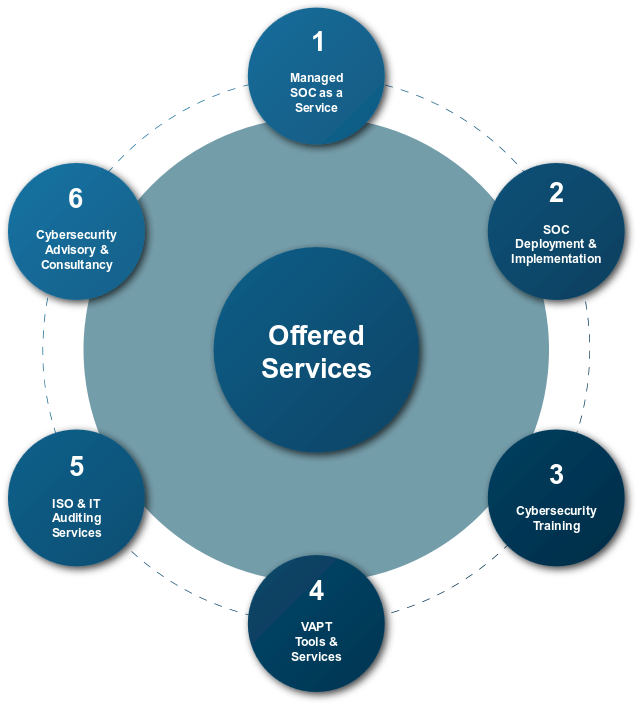
Flexible Deployment Models:
Offering Tailored On-Premise SOC Setup for dedicated control.
End-to-End Operational Excellence:
Covering the entire lifecycle from Requirements Analysis and Tool Selection to full System Integration and Go-Live.
Customized Playbook Development:
Creating Client-Specific Response Procedures and workflows that align with the client’s business processes and compliance mandates.
Continuous Improvement & Reporting:
Providing regular, detailed Performance Metrics (MTTD/MTTR) and leveraging Threat Intelligence to consistently tune the environment and mature security defenses.